The estimated reading time 3 minutes
Link part 1 powershell script to create aes encypted password string
Link part 2 powershell script to reconvert to plain password
Once a customer asked me how to store a password on local server and use it inside a powershell script to authenticate. Storing passwords in plain text is not the best solution, so I thought he should use a secure string. Yes, secure strings can be recalculated easy so another method for window dressing. Why not using a secure string encrypted with a individual encryption key, which can be stored on shares etc. This was the beginning of creating a small script that converts a password into two files. One text file with the encrypted string and the symmetric encryption key (AES256). For authentication you need both, keyfile and the textfile. You can also use these files on network shares for helpdesk admins or any other purpose.
NOTE: when you encrypt passwords with these method, you can use them in scripts, but anyone who can use google and has basic knowledge can make the password visible. PROTECT YOUR KEYFILE with special permissions. And if you loose it there is no way to recover it.
Let’s start with some basics:
Generating a random AES key in powershell:
$aeskeypath = ".\aeskey.key" $AESKey = New-Object Byte[] 32 [Security.Cryptography.RNGCryptoServiceProvider]::Create().GetBytes($AESKey) Set-Content $aeskeypath $AESKey
This code generates a unique AES 256 Bit key and stores it inside the file. Give a try! What can we do with this key? (by the way, there is no need to name that file .key, but for understanding reasons I use this).
See this links for further information:
https://docs.microsoft.com/en-us/dotnet/standard/security/cryptography-model
Password encryption with aes file
Now we are able to encrypt a password easily with this personal key.
Lets give a try:
$pw = Read-Host "type in a password!"-AsSecureString $pw $key = Get-Content .\aeskey.key $encryptpw = $pw | ConvertFrom-SecureString -Key $key #copy content to file Set-Content .\cred.txt $encryptpw
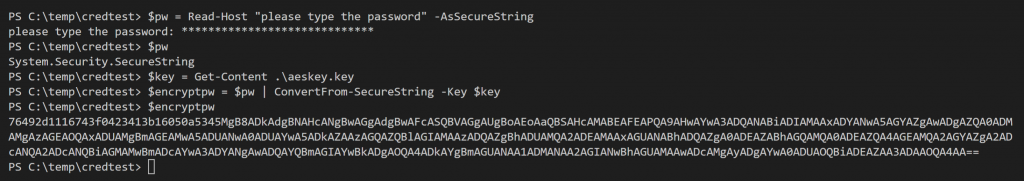
The variable $encryptpw contains your personal password encrypted with your personal AES 256 bit key. Not that bad!
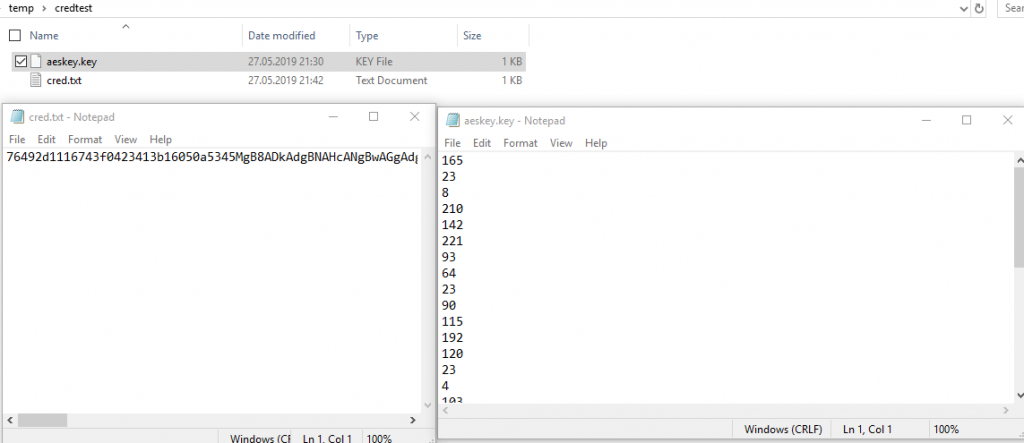
These are basic that I use in the following articles to store, encrypt, reuse passwords.
NOTE: If you change any character or format of these two files and have no backup, you won’t be able to get your password back.
I also want to show how you can use this method to authenticate to different services inside your powershell console. First the code:
$username = Read-Host "Type Username!" $AESKey = Get-Content .\aeskey.key $pwdTxt = Get-Content .\cred.txt $securePwd = $pwdTxt | ConvertTo-SecureString -Key $AESKey $creds = New-Object System.Management.Automation.PSCredential -ArgumentList $username, $securePwd $creds
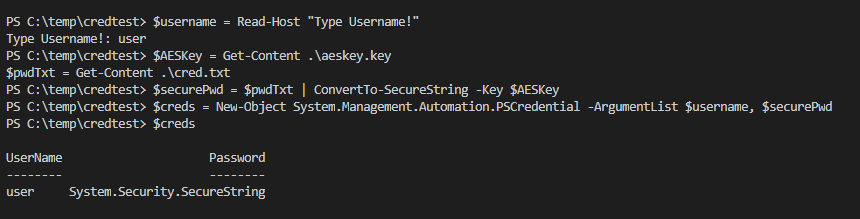
How to use credential objects
You can now use the object $creds to authenticate on exchange, ad, exchange online or other services. Let’s connect to exchange online with this method:
$Session = New-PSSession -ConfigurationName Microsoft.Exchange -ConnectionUri https://outlook.office365.com/powershell-liveid/ -Credential $creds -Authentication Basic -AllowRedirection Import-PSSession $Session -DisableNameChecking -Verbose
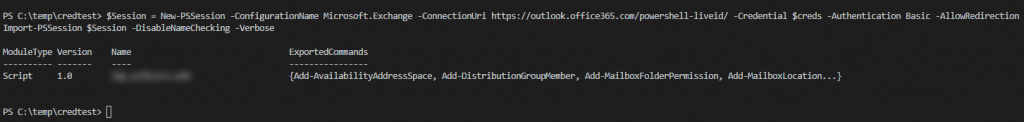
Now you are able to see what you probably can do with this small scripts.
I’ve made some scripts to automate the task of converting your password into two files.
Please let me know if you liked this article by clicking on “helpful”.
Link part 1 powershell script to create aes encypted password string
Link part 2 powershell script to reconvert to plain password