The estimated reading time 4 minutes
Windows Fileserver Ressource Manager (FSRM) update Ransomware List from multiple TXTs and compare via powershell
Lots of people today concerning about ransomware and how to prevent their network before encryption. There are quite few articels where you can find to configure fsrm on Windows File Server which does not allow special extensions for files etc. This is one method to reduce the impact of a ransomeware attack. So I asked myself, how is it possible to get up to date with the file extensions etc. because they are changing nearly every day.
For this reason I wrote a little powershell script which imports file extensions from multiple TXT-files, compares them and writes it in fsrm.
Before you can use this script you have to configure fsrm like the guy here
When fsrm is configured you can use my script to update your filegroup (tested with Windows Server 2012R2 and 2016)
https://github.com/blog-it-koehler-com/import-ransomware-extensions-fsrm
<#
.SYNOPSIS
script is used to import and summarize multiple txt files with file extensions in windows fsrm (fileserver ressource manager)
.DESCRIPTION
the script imports the content of txt files to fsrm. the txt files should look like the sample txt files in github.They have to be located
in the same directory. This directory should be defined in variable. Another variable is the filegroupname, you can see this in fsrm
.EXAMPLE
-
.Notes
-
this script does not create filegroup or filescreens etc.the current extensions configured will be saved in a legay txt file with date
further information on my blog: http://blog.it-koehler.com
---------------------------------------------------------------------------------
Script: import-fileextensions-v02.ps1
Author: A. Koehler; blog.it-koehler.com
ModifyDate: 21/01/2017
Usage:
Version: 0.2
---------------------------------------------------------------------------------
#>
#define variable
#path containing txt files (without '\' at the end!)
$txtfilepath = 'C:\Temp\ransomware'
#fsrm filegroup detecting ransomware
$filegroupname = 'Ransomware'
#########beginning of the script########
$date=((Get-Date).ToString('yyyy-MM-dd-HH-mm-ss'))
#export the existing extensions to legacy txt files
$legacyfile = (Get-ChildItem $txtfilepath -Recurse -Include '*.txt') | Where-Object {$_.Name -like "*-legacy-ext*"}
#check if legacy txt file available, if not create it, otherwise import txt files
if(!$legacyfile)
{
(Get-FsrmFileGroup -Name $filegroupname).IncludePattern | Out-File "$txtfilepath\$date-legacy-ext.txt"
}
#import content from txt files
$txtfiles = (Get-ChildItem $txtfilepath -Recurse -Include '*.txt').Name
#import content from all txt files inside directory
foreach ($txtfile in $txtfiles)
{
$txtfilescomplpath = $txtfilepath+'\'+ $txtfile
#convert all content to lower
$fileext += @((Get-Content $txtfilescomplpath).ToLower())
}
#sort and eliminate double entries
$compareext = $fileext | Sort-Object -Unique
Set-FsrmFileGroup -Name $filegroupname -IncludePattern ($compareext)
First you have to define two variables as seen in the section “define variables”. First the filepath where multiple txt-files stored with ransomware content. Next you have to define the filescreening name where powershell should import the extensions of the txt-files.
NOTE: if you have already configured and stored ransomware extensions in your fsrm, don’t worry. They will be exported in a legacyfile and imported with the appended extensions. So you will not loose your configuration. But be careful with other txt-files which store other content. The script does no research when importing the content.
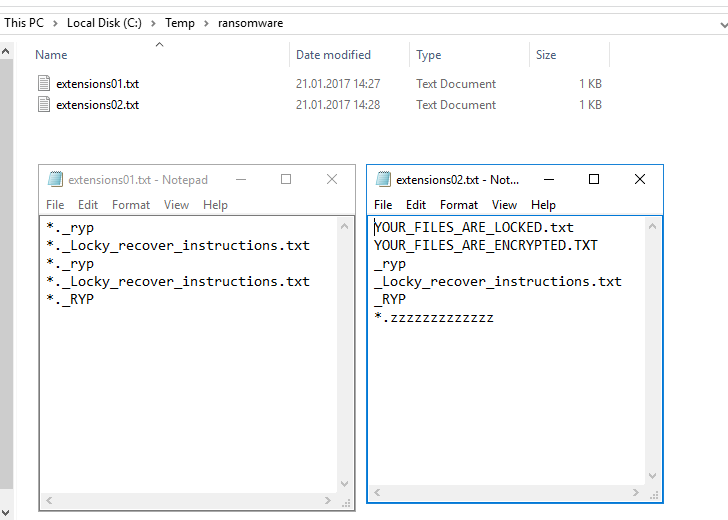
In my case multiple txt-files are stored in “C:\temp\ransomware”
My example includes some extensions more than one time, so I can test whether the script imports and compares them. (it also detects upper and lowercase duplikates). TXT-Files should look like this, because every row is a new extension for the script.
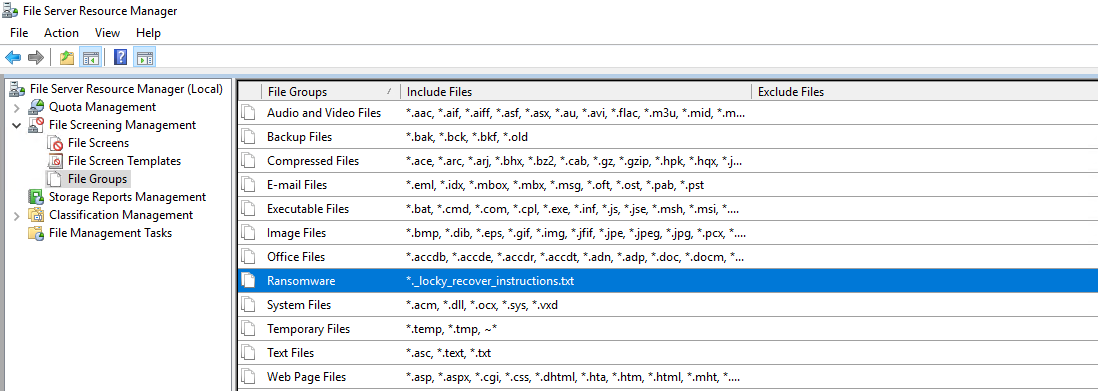
As you can see in the screenshot I already created the Filegroup “Ransomware”
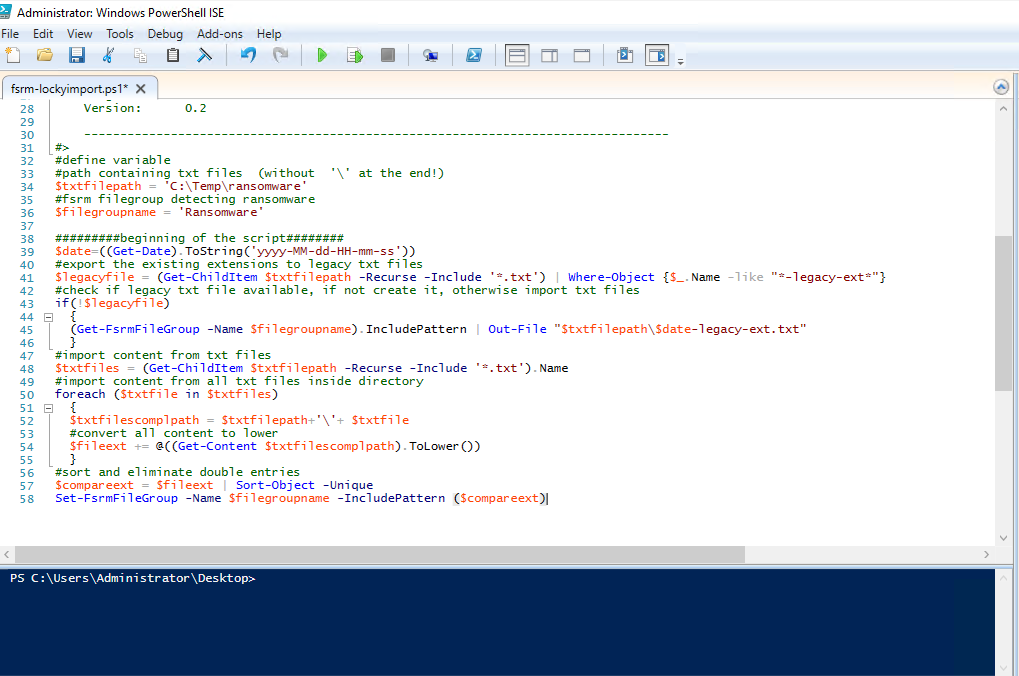
In the next step you can open Powershell ISE as Administrator an copy my complete script to the scripteditor.
If the variables are fine you can start the script with the green arrow.
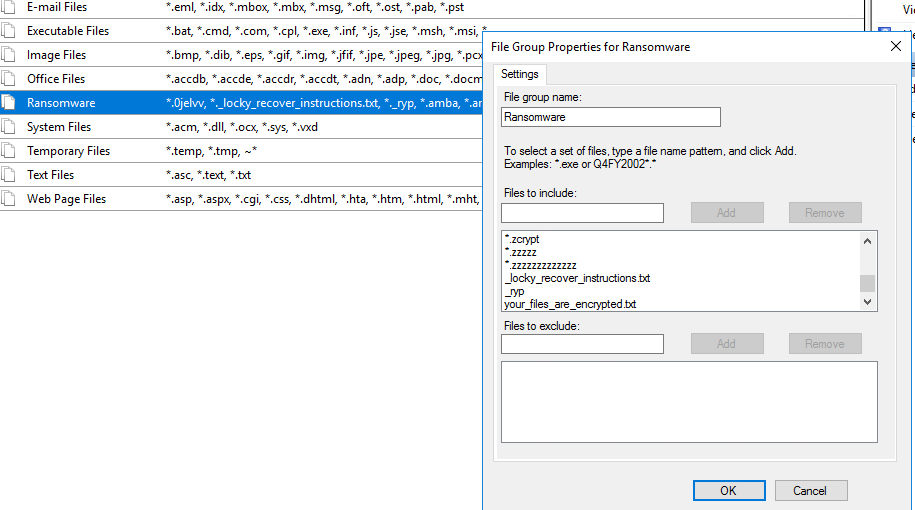
Have a look inside the fsrm and the filegroup you wanted to add extensions
After the script was executed you can find a legacy txt file next to your original txt files. The content is the old filegroup content
 It is possible to comapre multiple txt files from several providers to get a little more security to your fileserver.
It is possible to comapre multiple txt files from several providers to get a little more security to your fileserver.
Please write an comment if you have any further questions or feature requests.
Have fun.