The estimated reading time 2 minutes
Difference between PING and NSLOOKUP in combination with wildcard DNS records
hi everyone,
if you found this site, probably you are wondering about the special behaviour of nslookup and ping. Our customer found out that in his environment he pinged some websites in the internet everything works. If he gives the same website to NSLOOKUP a complete different ip address is returned. He had no problems reaching websites internal and external.
It turned out, that only NSLOOKUP returns false ipaddress, powershell and dns cache were fine.
Nevertheless I felt some discomfort and gave a search on this “strange” behavior.
The internal domainname is internal.customer.com
No other Forward Lookupzones are defined.
Outside the customer also can be reached with customer.com, so everything is bestpractices.
After some time of searching on DC and checking parameters I saw the external domain containing a wildcard dns record (see link ).
So the fog gives away on this “issue”. Wildcard DNS record means *.customer.com will be redirected to the website of the customer.
blabla.customer.com will be transfered to the website also.
NSLOOKUP works slightly different than other dns resolution processes, but what does it?
The focus on NSLOOKUP is NOT to resolve FQDNs, in other words NSLOOKUP appends the primary DNS suffix to every expression (also to FQDNs).
I sniffed the behavior and it looks like shown in the following screenshot:
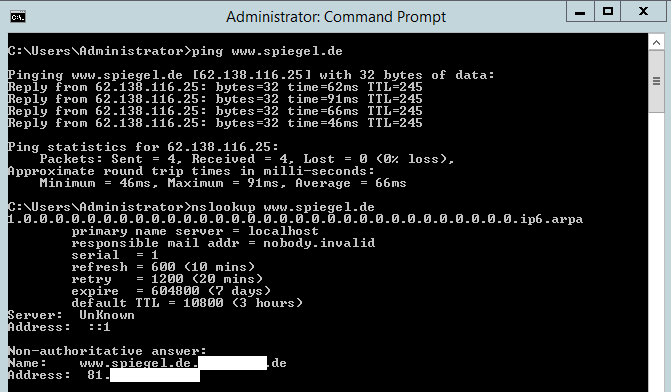
nslookup www.it-koehler.com
In CMD no error is shown and you can not see what NSLOOKUP does in the background. In reality it resolves www.it-koehler.com.it-koehler.com which does not exist on my external domain.
Now it was also clear why I found this “strange” behavior on customers side.
*.customer is the answer to any question of NSLOOKUP .
Ping or other dns queries know the TLD and resolves the right ipaddress.
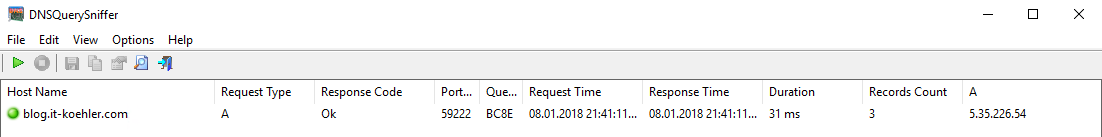
ping blog.it-koehler.com
There is one way to tell nslookup where the TLD ends and this is very simple. Just put a Dot at the end of the FQDN.
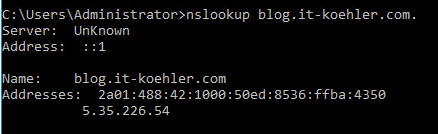
nslookup blog.it-koehler.com.
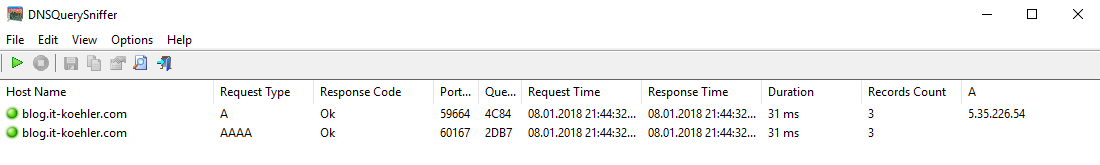
As DNS Sniffer I used DNSQerySniffer .
Hope this articel helps to understand NSLOOKUP.
Remember, for troubleshooting issues you should not use nslookup anymore, please use powershell with the cmdlet Resolve-DnsName
Link: https://docs.microsoft.com/en-us/powershell/module/dnsclient/resolve-dnsname?view=winserver2012r2-ps
Have fun.