The estimated reading time 1 minutes
Another very important security patch is enrolled the last 24 hours for Exchange 2013/2016/2019. See CVE-2021-42321. This CVE is also known als Remote Code Execution vulnerability.
If you want to know some more information about this Exchange Update and the vulnerabilities see this link:
https://techcommunity.microsoft.com/t5/exchange-team-blog/released-november-2021-exchange-server-security-updates/ba-p/2933169
Just choose your exchange version and download this patch from one of this links:
As seen in some patches before Exchange Online Organisations are not affected and have been patched already.
NOTE: If installing security patch manually you need to do it with an elevated prompt!!!
If you want to know whether you may already be attacked, have a look at your eventlog or use the following powershell script:
Get-WinEvent -FilterHashtable @{ LogName='Application'; ProviderName='MSExchange Common'; Level=2 } | Where-Object { $_.Message -like "*BinaryFormatter.Deserialize*" }
BTW: there is no need to install SU October you can directly install November SU KB
See also Exchange Build Numbers to get an overview to the latest exchange CUs and patches:
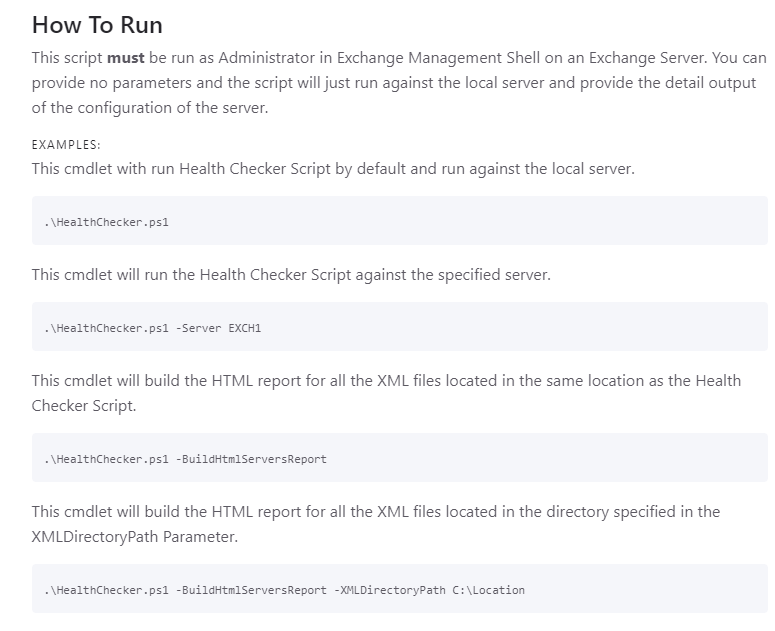
Another helpful tool is to use the Exchange healtchecker https://aka.ms/ExchangeHealthChecker


[…] Urgent Exchange 2019/2016/2013 Security Patch November … […]
[…] UPDATE 11/11/2021 link to november patch 2021 […]
after installed KB KB5007409Nov 21 patch ecp not working on exchange 2013 CU 23,
please help
Hi Afsar,
please check your AUTH certificate and maybe you have to renew it. See the following link:
After renewing the certificate givte it at least to hours(!!!) after this time your OWA and ECP should work normally. Outlook and ActiveSync should not have any connection issues during this time.
Greetings