The estimated reading time 3 minutes
NOTE: you can also use the code on exchange onpremises 2010 and above
A customer called me two weeks ago, that he got the feedback from his customer that he is sending some strange mails. So I had a look at the O365 security and clompliance center. After searching some reports I found out, that every E-Mail four users receive was redirected to a GMAIL address. The report also said that it was done with some inboxrules (the user never set up). Here some screenshots from the Azure Security Center and Compliance Center.
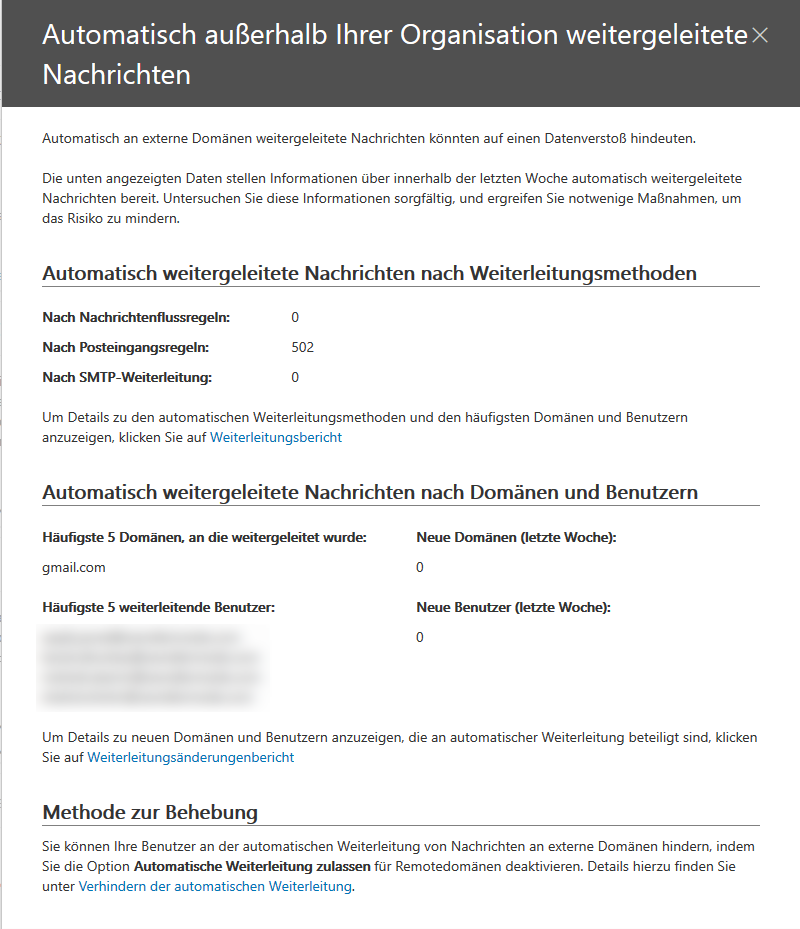
With this knowledge I needed to get deeper to remove these inbox rules. So I wrote a powershell oneliner to find the rule which fordwards mails to this gmail address. (needs an active connection to Exchange Online powershell (see my article O365 connector or use this LINK)
Get-InboxRule -Mailbox userwithfalseinboxrule@domain.com | Where-Object {$_.ForwardTo -like "*@gmail*"} | fl
I already knew what these inboxrules do to this user, so I created a short script to search all inboxrules from every O365 user which is forwarding to gmail. The result is written to a small text file.
$txt = "C:\temp\inboxrules.txt"
$emails = (Get-Mailbox).PrimarySMTPAddress
foreach($email in $emails){
"## Mailbbox: $email" |Out-File -FilePath $txt -Encoding utf8 -Append
Get-InboxRule -Mailbox $email | Where-Object {$_.ForwardTo -like "*@gmail*"} | select Name,ForwardTo,StopProcessingRules |Out-File -FilePath $txt -Encoding utf8 -Append
}
In the txt file I get every user with an inboxrule containing forwarding address with gmail. If there is no rule, nothing is logged, despite the mailbox name. The file looks like this:

As you can see the rules also had a special name they only consist of dots. So I searched also for “..” and got the same users as result.
$txt = "C:\temp\inboxrulesname.txt"
$emails = (Get-Mailbox).PrimarySMTPAddress
foreach($email in $emails){
"## Mailbbox: $email" |Out-File -FilePath $txt -Encoding utf8 -Append
Get-InboxRule -Mailbox $email | Where-Object {$_.name -like "*..*"} | select Name,ForwardTo,StopProcessingRules |Out-File -FilePath $txt -Encoding utf8 -Append
}
First step to do: Change the users password IMPORTANT, they probably have give their password to a phishing site. After change the password you can delete these rules. I also wrote a small script to handle this.
$emails = (Get-Mailbox).PrimarySMTPAddress
foreach($email in $emails){
Get-InboxRule -Mailbox $email | Where-Object {$_.ForwardTo -like "*@gmail*"} | Remove-InboxRule -Force
}
After the cleanup I recreated the inboxrule txt file and there was no rule to forward to gmail address anymore.

Also check your mailboxes forwarding addresses with the following powershell cmdlet:
Get-Mailbox -ResultSize unlimited | fl Name,*forwarding*
With the following code you can check all mailboxes forwarding addresses with the domain “gmail.com”
$searchdomain = "gmail.com"
Get-Mailbox -ResultSize unlimited | Where-Object {($_.ForwardingSMTPAddress -like "*$searchdomain*") -or ($_.ForwardingAddress -like "*$searchdomain*")} | fl Name,*forward*
If you want to clear all forwarding addresses with “gmail.com”, you can use this code:
$searchdomain = "gmail.com"
Get-Mailbox -ResultSize unlimited | Where-Object {($_.ForwardingSMTPAddress -like "*$searchdomain*") -or ($_.ForwardingAddress -like "*$searchdomain*")} | Set-Mailbox -ForwardingSmtpAddress $null -ForwardingAddress $null
If your O365 mailbox is blocked you may can cleanup and get it online again. If you like this blogpost, please click on “helpful”, if there are any questions just leave me a comment. Have fun finding the evil inboxrules.