The estimated reading time 4 minutes
Some days ago Microsoft announced the final ending of basic authentication in Exchange Online.
Today, we are announcing that, effective October 1, 2022, we will begin to permanently disable Basic Auth in all tenants, regardless of usage, with the exception of SMTP Auth.
https://techcommunity.microsoft.com/t5/exchange-team-blog/basic-authentication-and-exchange-online-september-2021-update/ba-p/2772210
So why disabling Basic Auth? It works like a charm!
Basic authentication have been used for many years for different kind of clients and services in Exchange and other services. It is simple to setup and credentials often are saved on devices so no promts disturb users experience.
The other thing is, that basic auth is not that secure, especially without TLS encryption, attackers can gain credentials much more easier compared to modern authentication. Implementing MFA (Multi Factor Authentication) can be painful and not that easy so Microsoft decided to remove basic auth.
Basic Authentication is an outdated industry standard, and threats posed by Basic Auth have only increased in the time since we originally announced we were making this change.
https://techcommunity.microsoft.com/t5/exchange-team-blog/basic-authentication-and-exchange-online-september-2021-update/ba-p/2772210
What is Microsoft doing now?
Microsoft started disabeling basic auth already for tenants not using it. And beginning in the year 2022 basic auth will also be disabled for tenants who still use it (period 12-48 hours). So all protocolls excepting SMTP AUTH will be affected (POP,IMAP,ActiveSync…). As an admin you can re-enable basic auth again with a selfservice tool. You can also use this short link, to do the test and re-enable Basic Auth:
https://aka.ms/PillarEXOBasicAuth
You can also type the following string into your help search in M365 admin portal:
Diag: Enable Basic Auth in EXO
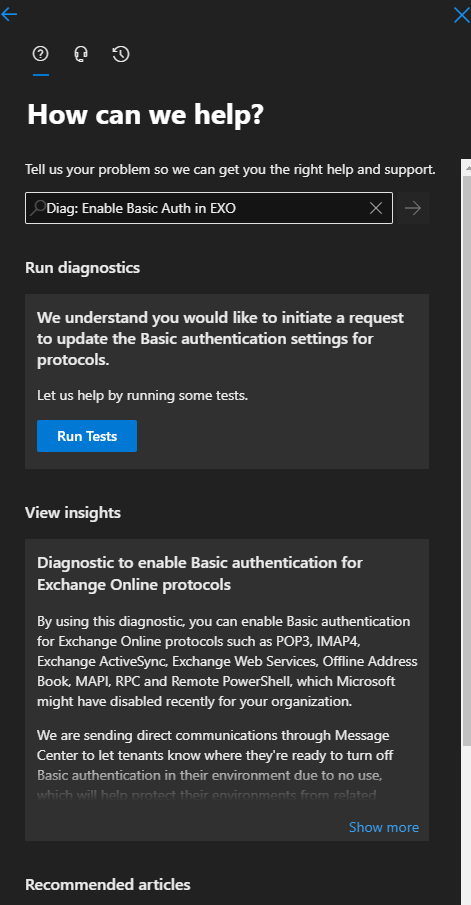
After running the test you can choose which protocol you want to exclude.
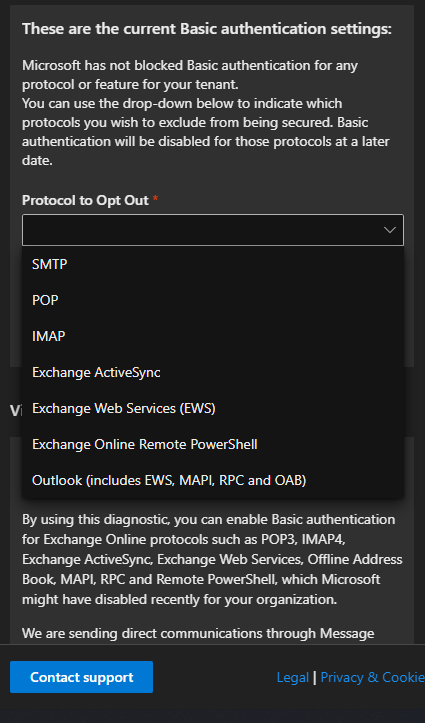
You already did disabling basic auth, your message should look like this:
Do I have to intervene?
It depends! According to my experience basic auth is often used in powershell scripts against exchange online. I would recommend to check these scripts.
If there are some legacy outlook clients (2010)/services who use POP/IMAP/ActiveSync or other protocols with basic authentication, they simply don’t work after disabling.
If you use Modern Authentication everywhere, you have to do nothing at all. This is not affected.
NOTE: if you don’t use basic auth, please disable it! See the section below.
How to find Basic Auth Logins?
One simple Method is to go to Azure Active Directory admin center and see last logins like this:
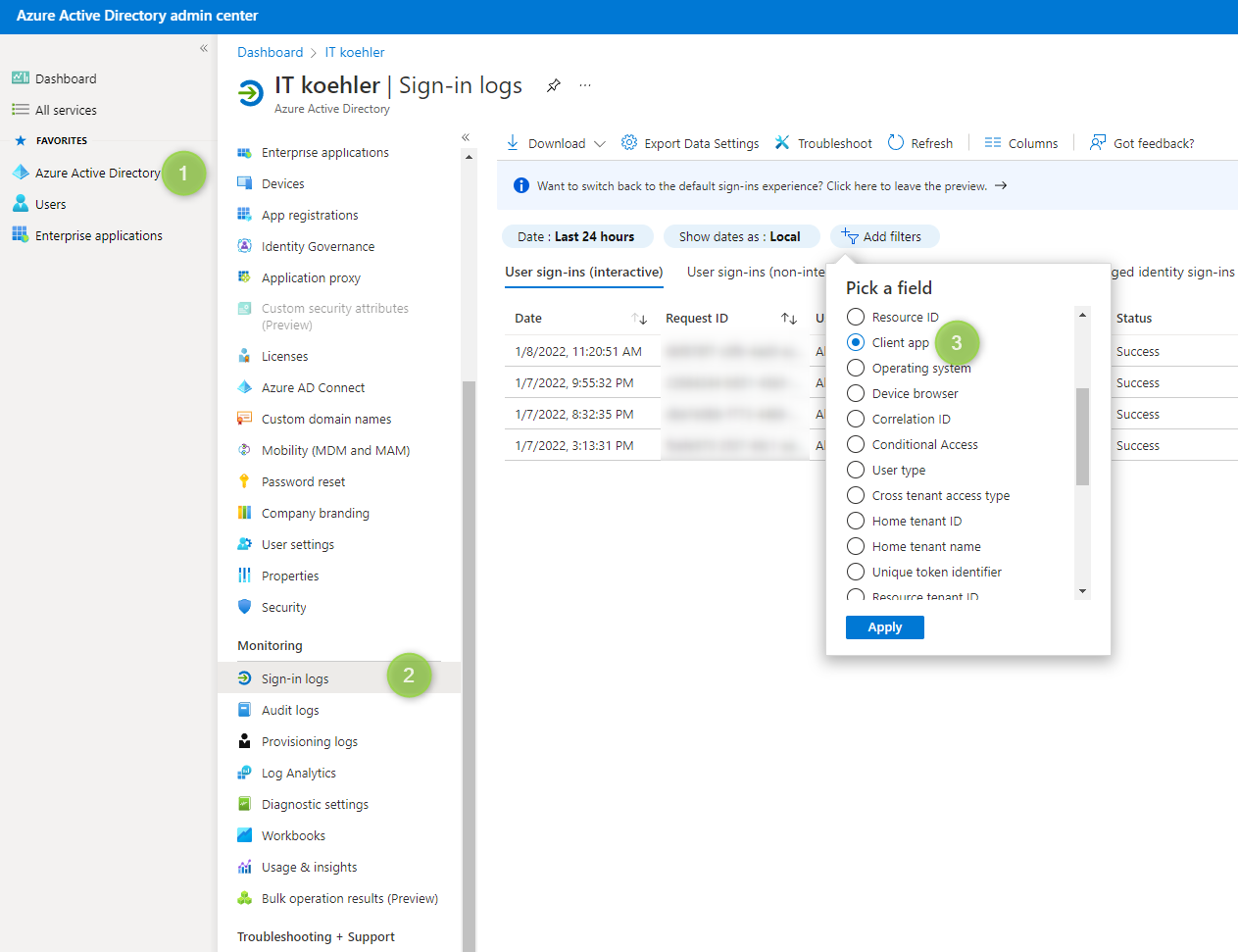
Select all legacy client apps

Don’t forget to change “date” filter checking the lase few days and in my tenant there is a basic auth indeed.

In my case this is an old Android Client (Android DECT telephone) used to sync contacts, but this device will be replaced.
How to shutdown this old trash?
You can disable old basic auth also in Azure Active Directory admin center and go to “properties”:
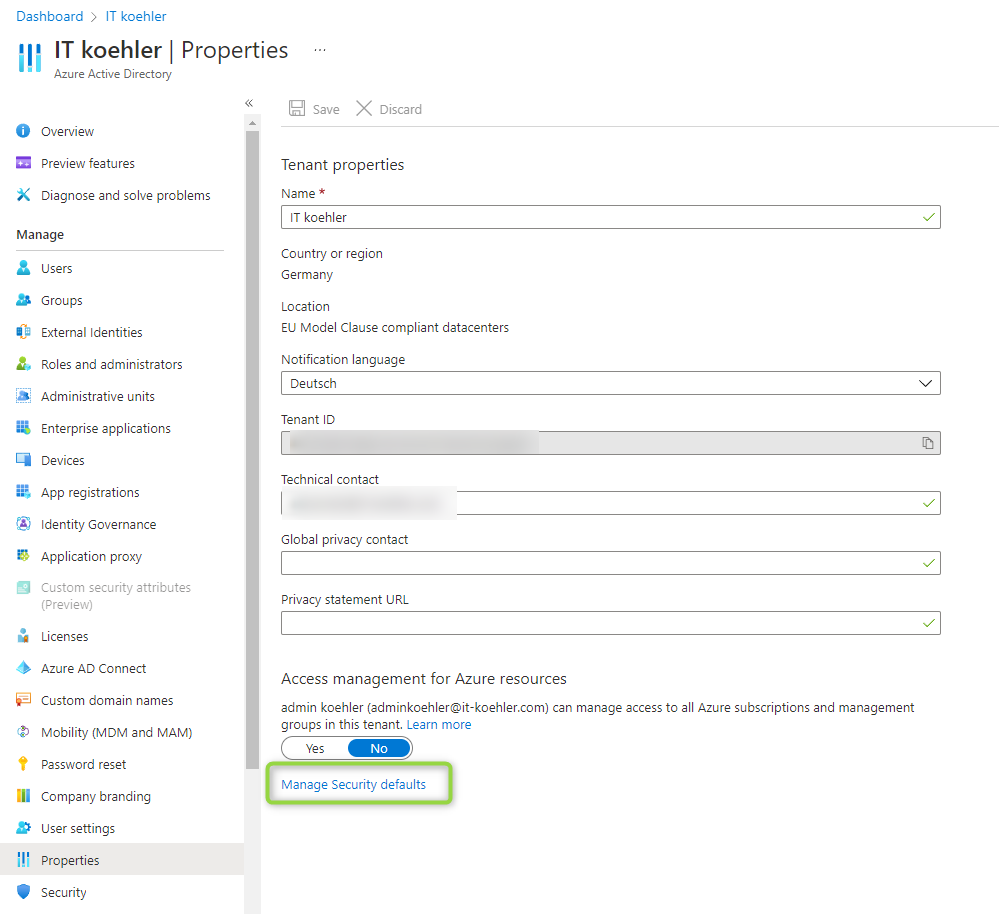

Enable Security Defaults and save and Basic Auth is disabled permanently. You can check now via help if Basic Auth is disabled
https://aka.ms/PillarEXOBasicAuth
Additional outlook information
If you found some old Outlook 2010 clients, they use Basic Auth and they are not able to use Modern Authentication.
Check also your Outlook 2013 client installations, if they don’t use modern auth you need to deploy the following registry keys to all of your outlook clients:
| Registry key | Type | Value |
|---|---|---|
| HKCU\SOFTWARE\Microsoft\Office\15.0\Common\Identity\EnableADAL | REG_DWORD | 1 |
| HKCU\SOFTWARE\Microsoft\Office\15.0\Common\Identity\Version | REG_DWORD | 1 |
If there are some issues with newer versions of outlook have a look on the following link:
| Registry key | Type | Value |
|---|---|---|
| HKEY_CURRENT_USER\Software\Microsoft\Exchange\AlwaysUseMSOAuthForAutoDiscover | REG_DWORD | 1 |
Some questions? Let me know in the comment section. If you like it, please click on helpful.
Happy disabling!