The estimated reading time 3 minutes
Unfortunately, the topic of passwords is still taken lightly in many areas. The National Institute of Standards and Technology (NIST) provides some guidelines on passwords, as well as alternatives to passwords such as hardware tokens and smart cards, or generally phishing-resistant authentication methods. Microsoft offers an illustrative schema as a graphic here:

To operate with a reasonable level of security in the field of authentication, a FIDO2 key or smart card is necessary as of today, especially for highly privileged accounts. The NIST document also highlights the importance of phishing-resistant multi-factor authentication methods (such as FIDO2).
For more information on FIDO2, click here.
Password Requirements
Back to the topic of passwords, or “the old way of auth.” Here is the LINK to the NIST Website SP 800-63B.
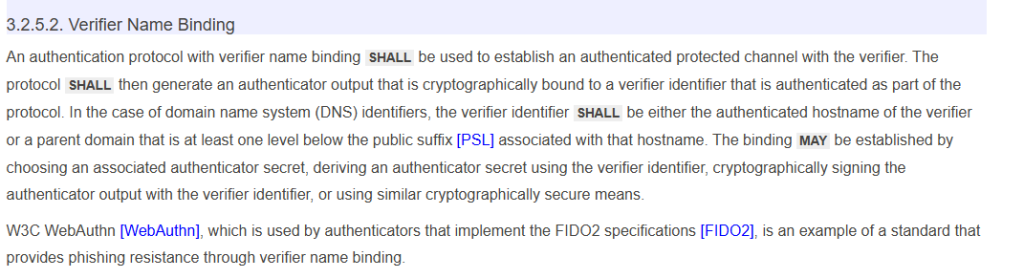
In section 3.1.1.2, “Password Verifiers,” it discusses password requirements and provides some guidelines on the conditions for processing passwords.



Password Requirements
I will try to summarize the essential points regarding passwords:
- MUST have at least 8 characters.
- SHOULD have at least 15 characters.
- SHOULD allow the creation of passwords with at least 64 characters.
- SHOULD allow the ASCII character set.
- SHOULD allow the Unicode character set.
- SHOULD NOT impose a mix of different character types.
- SHOULD NOT require periodic password changes.
- SHOULD NOT use security questions to bypass passwords.
- MUST be checked against password lists (blocklists) when changed or created (if found, the password must not be used and a new one must be defined).
- MUST provide a message explaining why the password cannot be used if it is found on a blocklist.
- MUST integrate a limit on login attempts.
- MUST be transmitted over an encrypted channel when changed or created.
- MUST allow the use of a password manager and the copy-paste function.
- MUST verify the entire password (in some cases, passwords are only checked up to a certain point, and everything after that is truncated see example 1 or example 2).
Strategy
What is the right strategy to create and use secure passwords? There is a very good video by BSI on YouTube about this (german only).
In this video, two variants are presented: either at least 8 characters cryptic and with four different character types, or as long and simple as possible, like a complete sentence with two different character types.
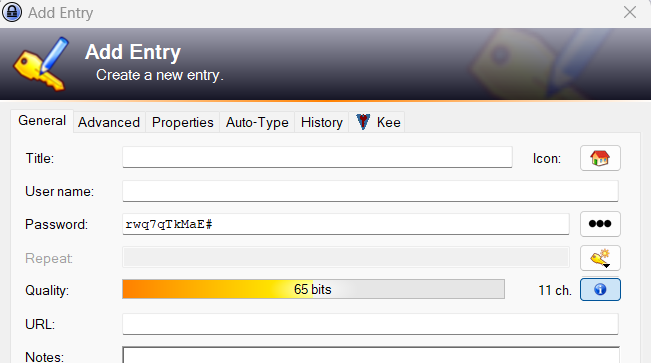
Example Variant 1: rwq7qTkMaE#
In the password manager, this password is already declared as “moderate,” but according to NIST, it would be acceptable.
Example Variant 2: Beim_Schreiben_dieses_Artikels_habe_ich2mal_pausiert
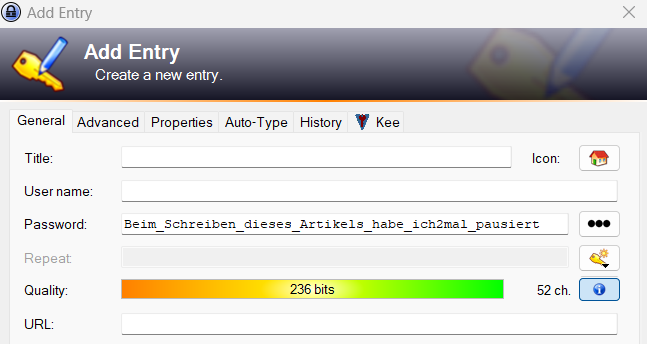
Even if the underscores are removed, the password is still significantly more secure than the cryptic password from Variant 1.

Conclusion
Please do not use short, simple passwords from password lists like Kaonashi, as there are good ways to create long and secure passwords. And one more request: USE A PASSWORD MANAGER.

Here is a small excerpt from the Kaonashi password list, specifically the first 100 entries. If anyone is using any of these passwords, I strongly advise changing them immediately.
Note: The list contains 866 million entries!
123456 123456789 qwerty password 12345 qwerty123 1q2w3e DEFAULT 12345678 111111 1234567890 1234567 123123 000000 30media qwertyuiop 10pace 24crow 59trick 59mile 19weed abc123 66bob 123321 1q2w3e4r5t )ryan 654321 666666 1234 password1 qwe123 7777777 asdasd 123 iloveyou 1q2w3e4r 555555 1qaz2wsx 123qwe zxcvbnm 987654321 123456a 121212 qazwsx 112233 homelesspa dragon 159753 777777 1234qwer monkey 123123123 11111111 222222 qwerty1 asdfgh asdasd123 gfhjkm 123654 a123456 asdfghjkl yuantuo2012 123456q 999999 qwert zxcvbn 1111111 88888888 qwer1234 Password q1w2e3r4t5 11111 aaaaaa 123abc 0987654321 xxx 123456789a x4ivygA51F q1w2e3r4 qazwsxedc football 3rJs1la7qE 131313 samsung 789456123 1111 12345a 1234561 888888 333333 fuckyou 159357 789456 qweasdzxc 987654 master qweqwe 12344321 princess sunshine
In this sense, I hope I have shed some light on the topic of password security and look forward to your comments.