The estimated reading time 2 minutes
Most of the time, I’m searching for new products and software which makes life easier but has no lack of security. One of this product (in my personal opinion) is YubiKey from Yubico.
In this article I’m describing some basic settings and also some use cases for additional authentication with the YubiKey. First we need to download the YubiKey Manager:
https://www.yubico.com/support/download/yubikey-manager/
Lots of web services are using FIDO2 as authentication protocol, thats why I’m going to show some examples how to use it. If you are searching for a list of supported provides, see this link:
https://www.yubico.com/de/works-with-yubikey/catalog/?sort=popular
If you are searching for a deeper look behind different (german only)
https://thomas-leister.de/authentifizierungsverfahren-des-yubikeys-erklaert/
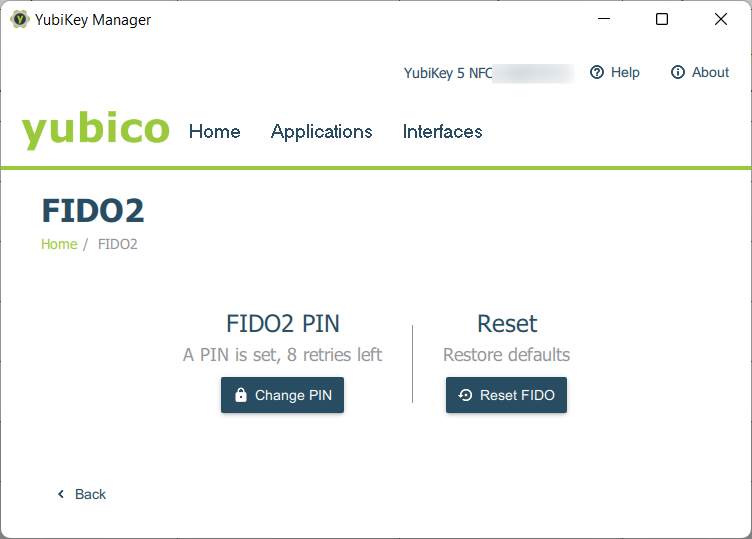
NOTE: using RESET kills all data stored on yout YubiKey, so be careful!
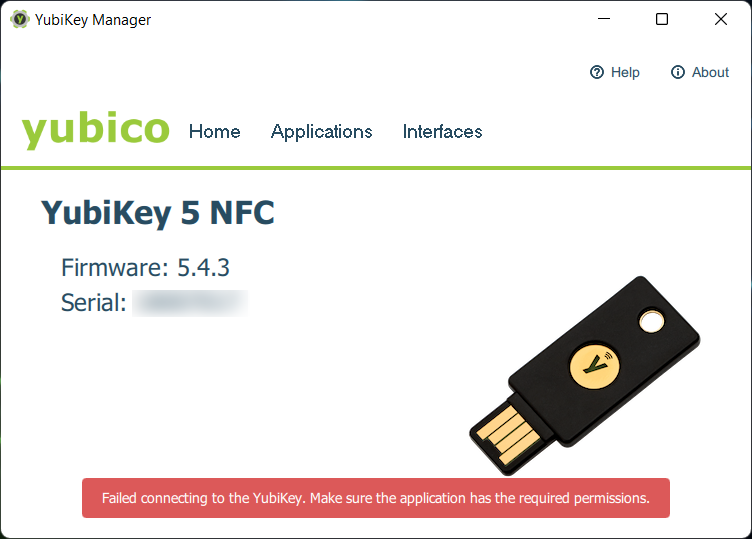
If you have the following error ” Failed to connect…” you need to execute YubiKey Manager “as administrator”.
After PIN setup you can start using your key directly.
It’s worth to have a short look on Interfaces where you can define which interface and protocol is available and can be used.

That’s it for setup now, let’s start to test the YubiKey with some web services. For first try let’s use Twitter, because I don’t use twitter that much so this is the perfact candidate. Of course there should be multifactor auth available and active.
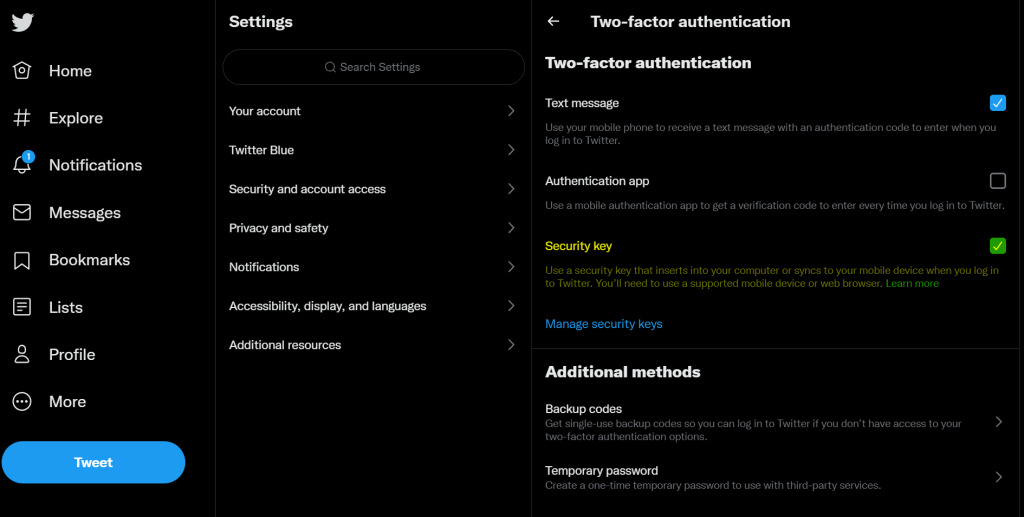
Add your YubiKey with the PIN you configured before and now you can use it as second authentication method for login to twitter.
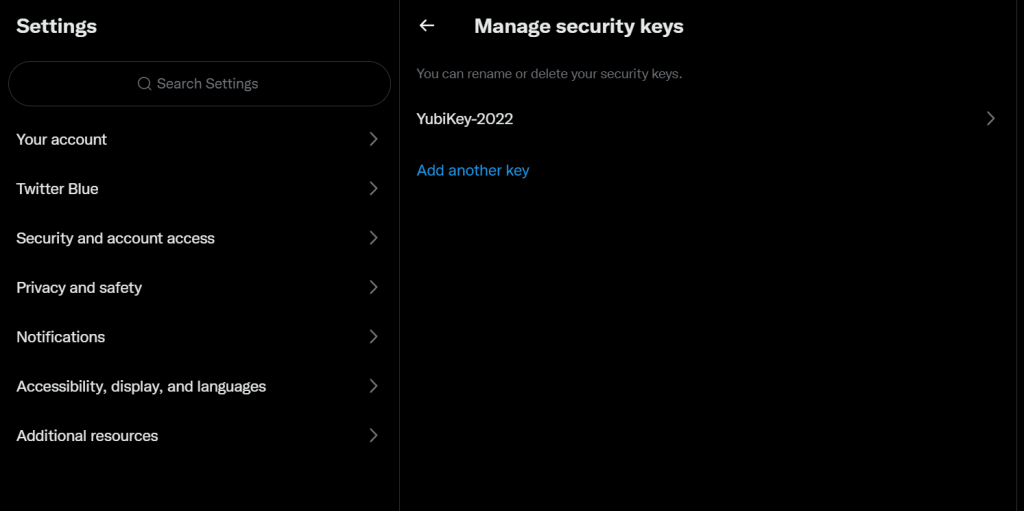
That was easy, so there is another candidate to test. Facebook.
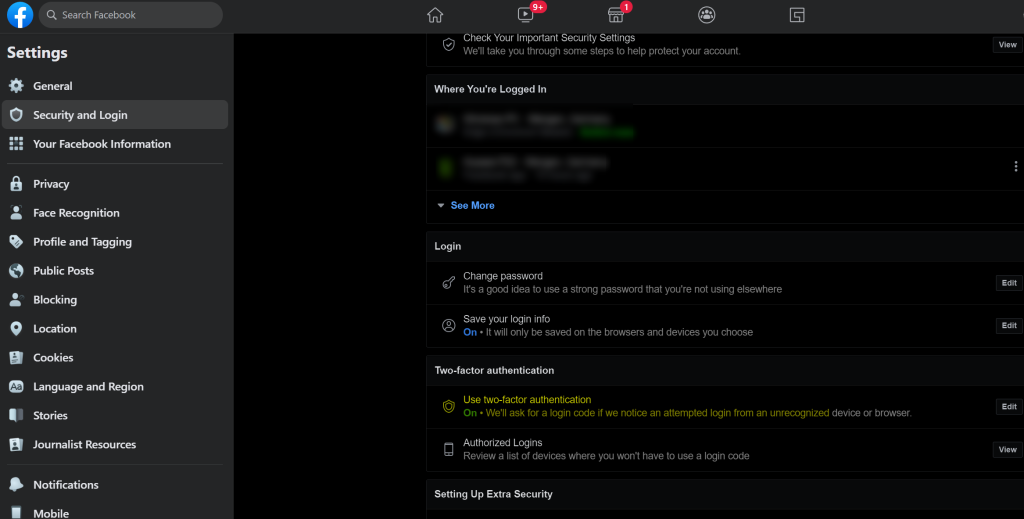
First disillusionment took me back to reality (no big deal). With the most current version of MS Edge key registration was not available, but Google Chrome did the job.
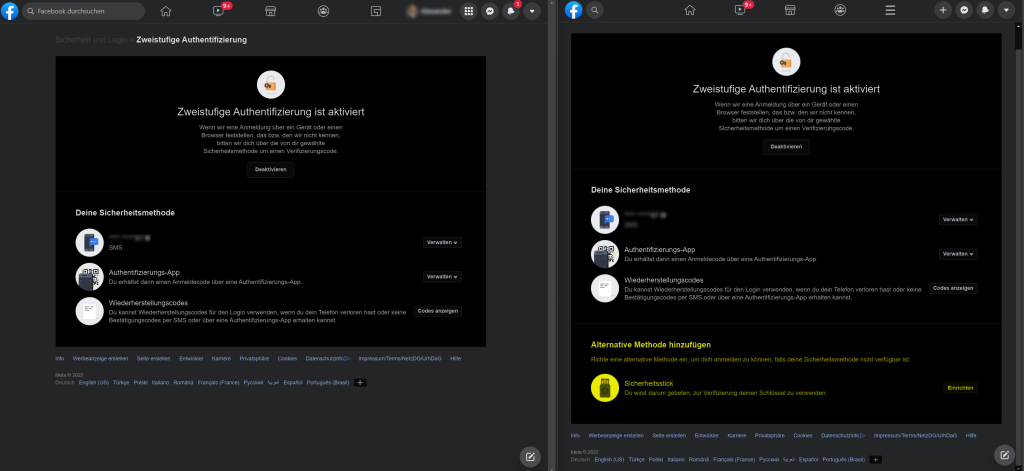
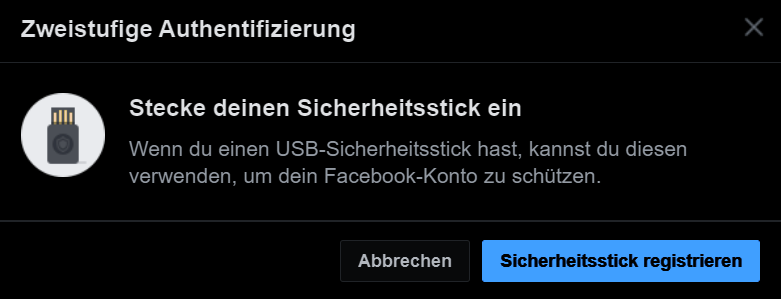
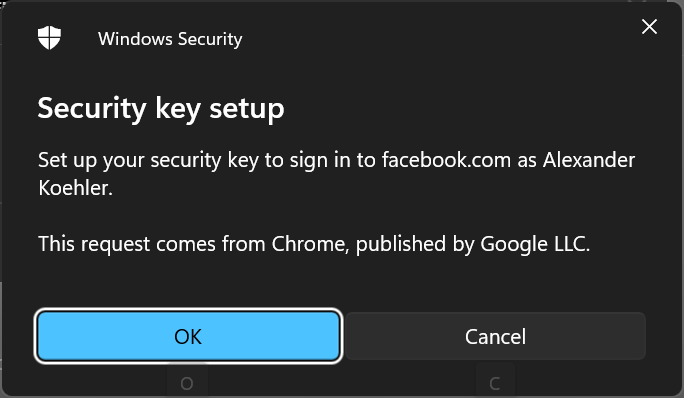
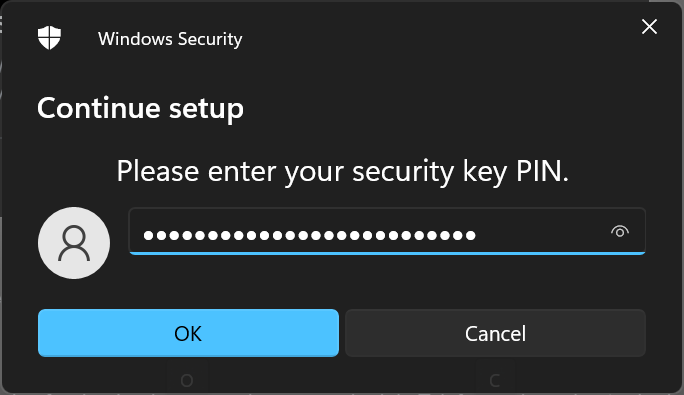
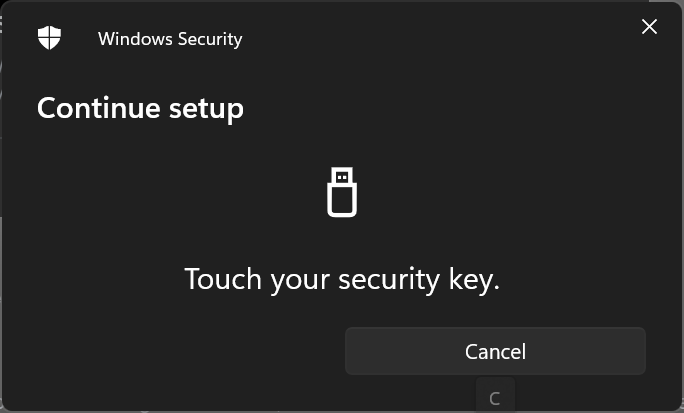
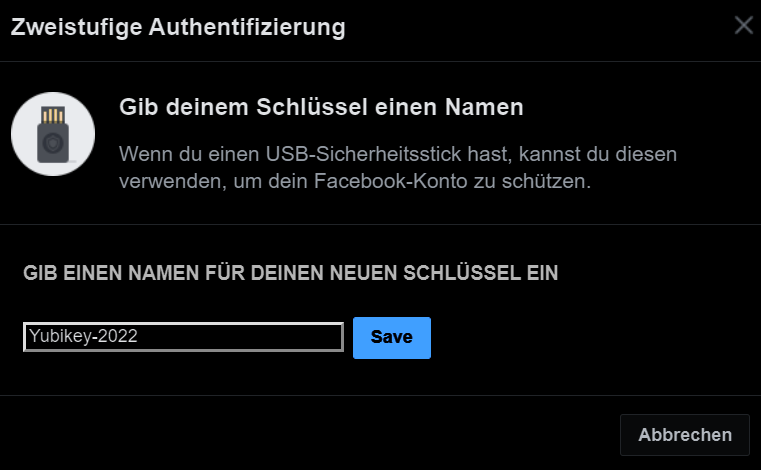
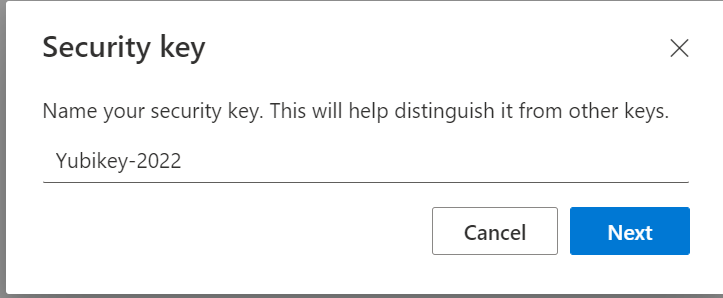
Just define your key name and you are done.
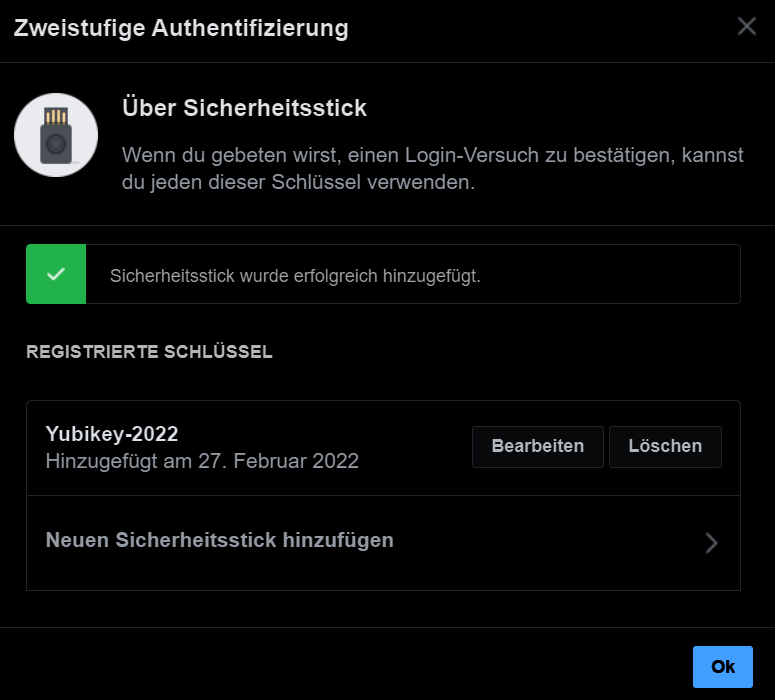
Microsoft Account (Business)
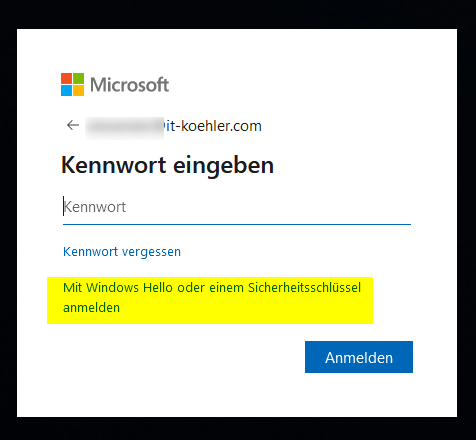
One of my important accounts is my Microsoft account, let’s secure this account also and get to your sercurity settings. https://mysignins.microsoft.com/security-info
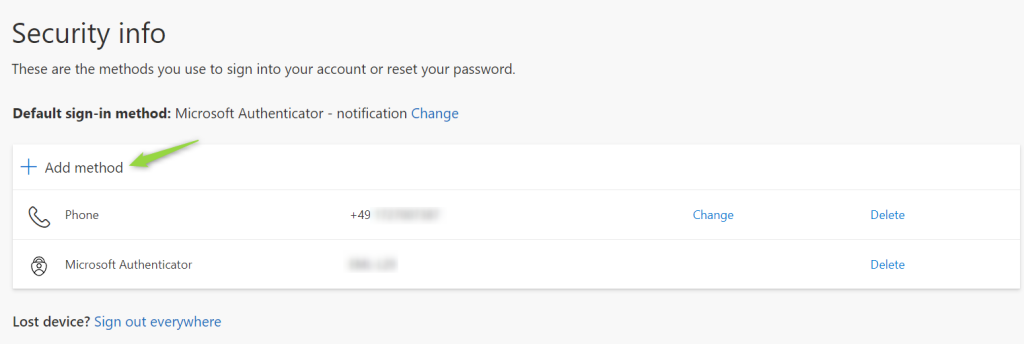
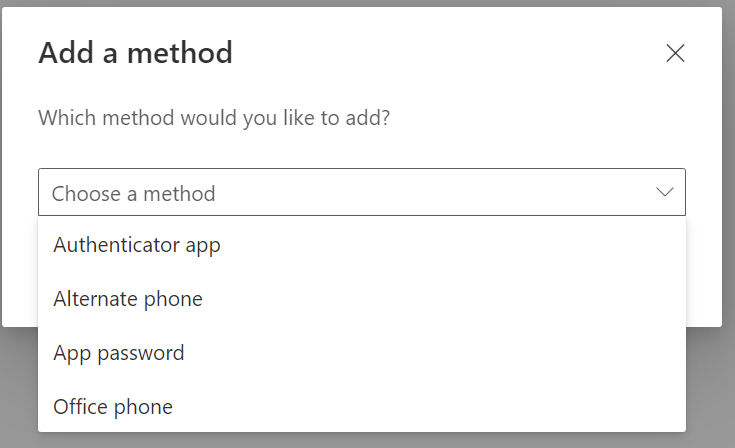
If you want to have some additional information activating FIDO2 security keys see this link.
https://docs.microsoft.com/en-us/azure/active-directory/authentication/howto-authentication-passwordless-security-key
Enabling FIDO 2 security settings can be done in M365 admin center only. https://aad.portal.azure.com/
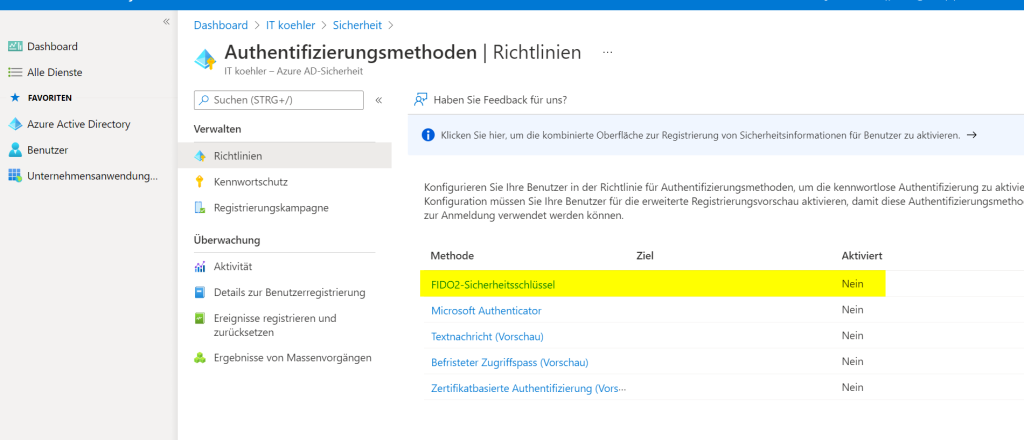
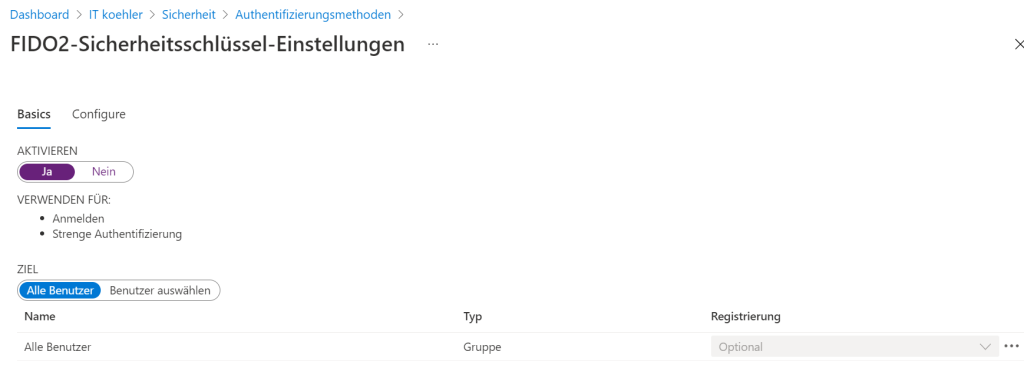
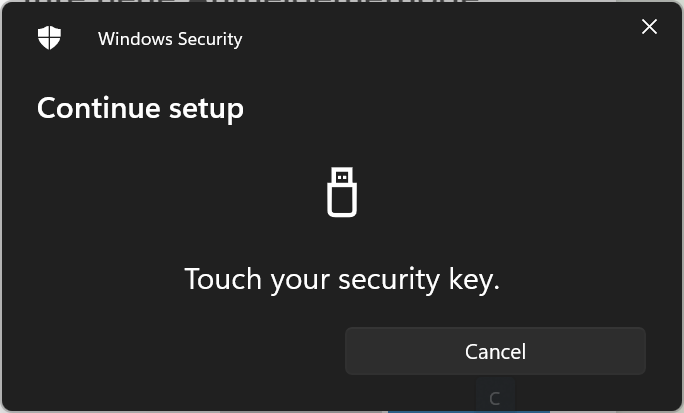
Got back to my normal account and access the security portal one again, you should be able to access security key option.
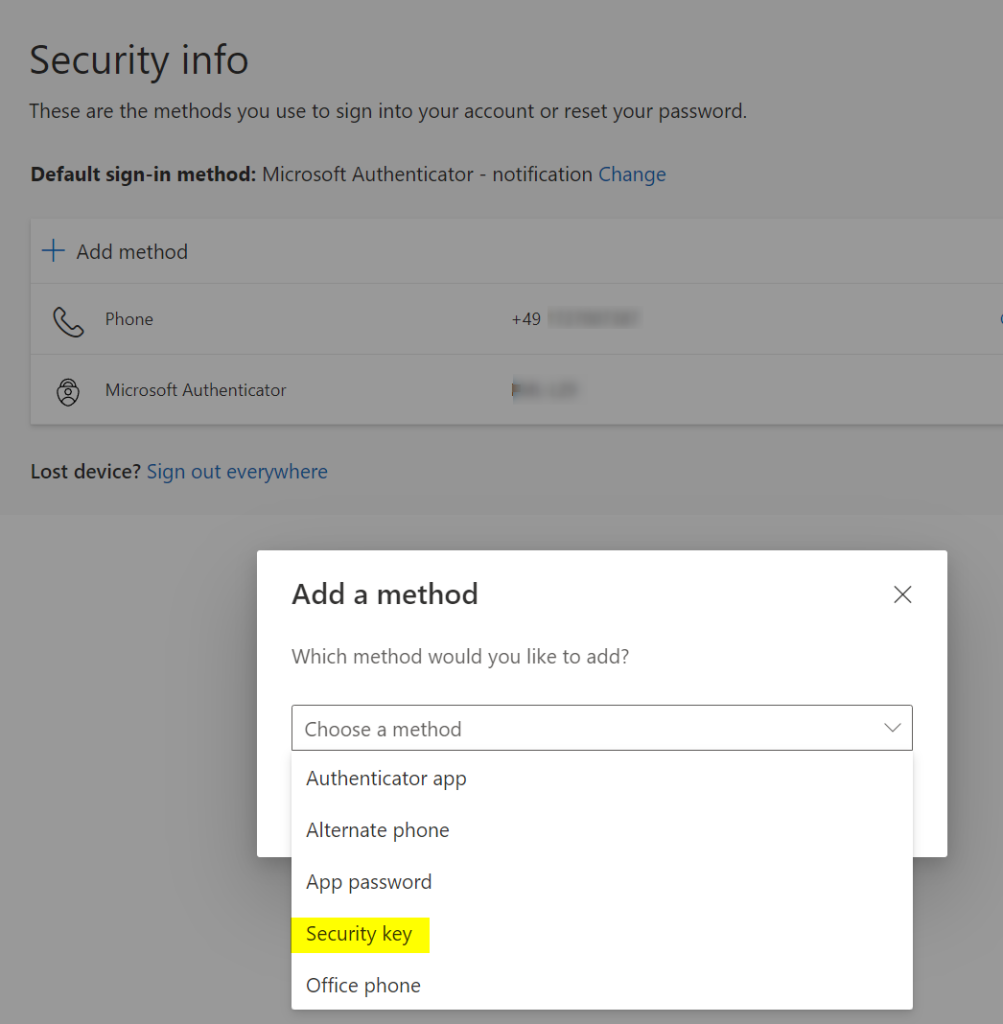
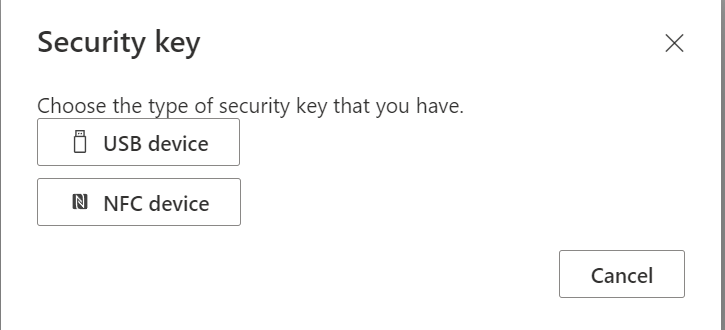
In my case I’m choosing USB device because my YubiKey is connected via USB interface.
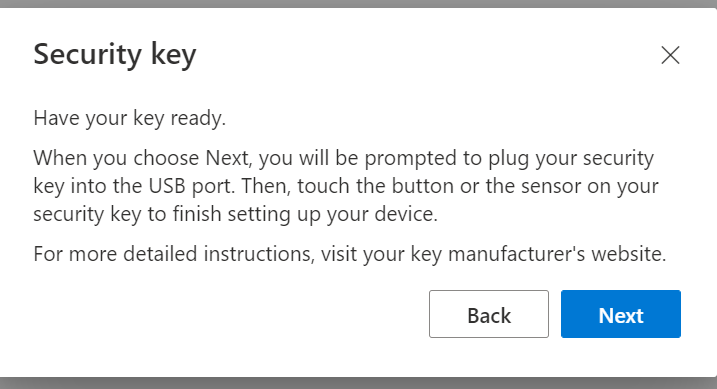
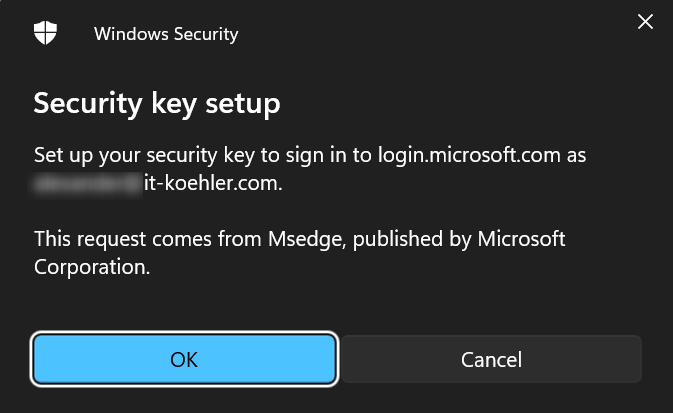
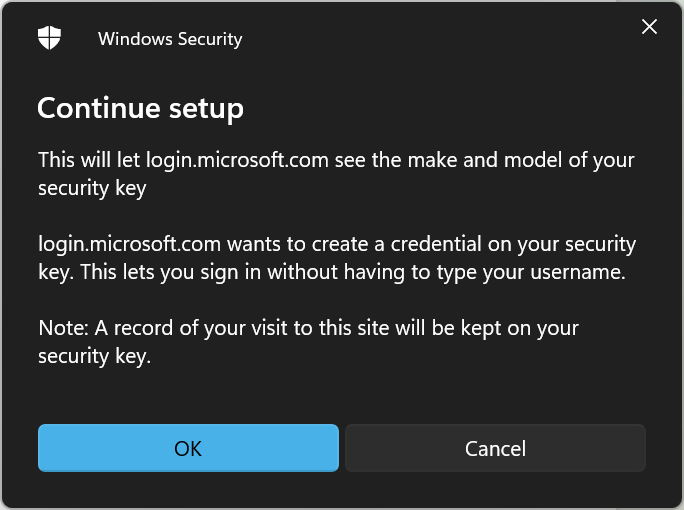
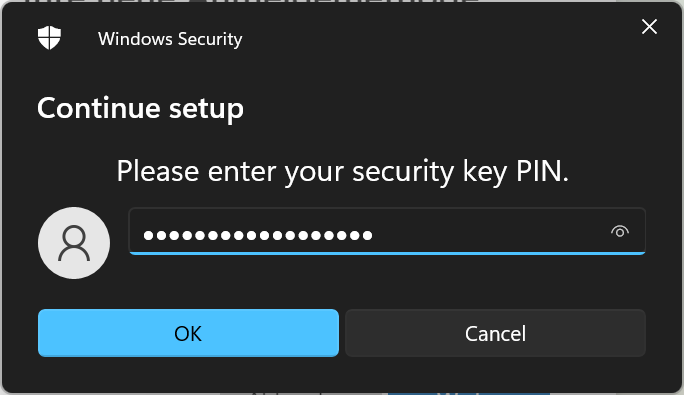
Have fun accessing accounts with YubiKey and join the modern way of multifactor auth.
If you like this article, please click on “helpful”.


[…] (NIST) provides some guidelines on passwords, as well as alternatives to passwords such as hardware tokens and smart cards, or generally phishing-resistant authentication methods. Microsoft offers an […]
[…] Multifactor Auth like a boss using YubiKey Part 1 […]